Reviewsnap - Setting up LDAP Authentication
Reviewsnap can integrate with most single sign-on providers via LDAP.
LDAP (Lightweight Directory Access Protocol) is a protocol used primarily by Microsoft services, like Active Directory (AD), to locate user accounts, organizations, and other resources. Reviewsnap can integrate with any LDAP or LDAPS server, allowing you to connect Reviewsnap to your organization’s existing directory. Upon login (on our standard login page), Reviewsnap will check usernames and passwords against your LDAP server, keeping these credentials in sync with Reviewsnap.
Single sign-on is an advanced Reviewsnap feature, and is only available in the Pro plan. If you would like to add this feature to your organization’s account, please contact us at help@reviewsnap.com.
NOTE: Reviewsnap is a cloud-based application, and our servers must be able to communicate with your LDAP server. If your LDAP server is protected by firewalls or additional network security, your organization must allow Reviewsnap’s servers access. Our application does not support connecting to your organization’s VPN or local network. For more information, please contact help@reviewsnap.com.
There are four steps to setting up LDAP authentication in Reviewsnap:
- Configuring LDAP within Reviewsnap
- Testing the configuration
- Enabling LDAP authentication for all users
1. Configuring LDAP within Reviewsnap
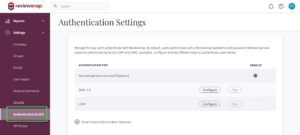
Reviewsnap requires the following information to set up LDAP authentication, which you can enter by visiting Settings > Authentication & SSO:
Host
Endpoint or IP address of your LDAP server.
Examples:
- 54.176.31.140
- ldap.reviewsnap.com
Port
This is generally 389 for plain connections, and 636 for SSL/TLS.
Method
SSL/TLS or Plain. SSL/TLS is highly recommended, but Reviewsnap can communicate over an unencrypted (plain) connection.
Bind DN
Account username or fully-qualified DN Reviewsnap will use to perform LDAP lookups.
Examples:
- reviewsnap
- username@reviewsnap.com
- CN=Reviewsnap Read,CN=Users,DC=reviewsnap,DC=com
Password
Password for the bind username or DN above, securely stored and never displayed.
Base DN
Base DN to used to find users.
Examples:
- DC=reviewsnap,DC=net,OU=Salary Employees
- dc=reviewsnap, dc=com
UID
LDAP attribute corresponding to the username on the login form, usually sAMAccountName or userPrincipalName. This is not required when using the optional Search Filter below.
LDAP Search Filter
Used to identify users in place of UID above. The string %{username} will be interpolated by the value entered by the user.
Examples:
- (sAMAccountName=%{username})
- (&(uid=%{username})(memberOf=cn=myapp-users,ou=groups,dc=example,dc=com))
- (&(objectCategory=person)(objectClass=user)(!(cn=andy)))
- (sn=sm*)
- (&(objectCategory=person)(objectClass=contact)(|(sn=Smith)(sn=Johnson)))
- (&(objectClass=user)(sAMAccountName=%{username})(|(memberof=CN=Employee A-L,OU=Salary Employees,DC=reviewsnap,DC=com)(memberof=CN=Employee M-Z,OU=Salary Employees,DC=reviewsnap,DC=com)))
Enter the above information into Reviewsnap, and proceed to the next step.
3. Testing the configuration
Follow the instructions to test the configuration in Reviewsnap, opening the provided URL in a separate browser or incognito window so that it’s not affected by your current session with our application.
If sign in is not successful, you can click “Show Failed Authentication Attempts” from the Authentication Settings page to see more detailed error messages.
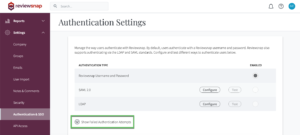
Here are some tips to resolve common issues with LDAP:
Operation timed out
Reviewsnap tried to issue a request to your LDAP endpoint, but never received a response. You might consider:
- Double-checking your Host and Port are correct
- Making sure your LDAP endpoint is publicly accessible, or you’ve allowed Reviewsnap’s servers through the necessary network security (see NOTE at top of this article)
Bind failed
Reviewsnap “binds” to your LDAP server with the Bind DN and Password provided. If that fails, it can mean one of several things:
- The Bind DN is not correct
- The Password for the Bind DN is not correct
- The LDAP server refused the connection from Reviewsnap for some other reason
getaddrinfo: nodename nor servname provided, or not known
Reviewsnap had issues resolving the host name of your LDAP endpoint. Consider using an IP address instead, as this is usually caused by issues with DNS.
User has not been added to Reviewsnap
Automatically provisioning users can result in multiple accounts for the same user, or your users not having access to the right information – both which can be difficult to correct. For these reasons, Reviewsnap only authenticates users that have already been added to the application, and will not automatically create accounts for new users. Users can be added manually for smaller organizations, or using the User Import, for easier management of users in bulk.
If a user successfully authenticates with your chosen login strategy, but an account with that username (a.k.a “login”) cannot be found, they will receive a “User has not been added to Reviewsnap” error.
4. Enabling LDAP authentication for all users
Once you have sufficiently tested the ability to log in via LDAP, you can enable it for all users in your organization by selecting LDAP as the enabled authentication type.
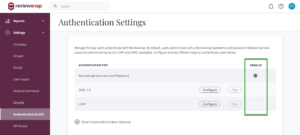
Once LDAP is enabled as the way your users authenticate, you’ll notice that passwords can no longer be set or recovered within Reviewsnap.
.png)